Expert Interviews
- University Reviews
- Career Guide
 Video Counseling
Video CounselingImportant Facts
- Ask any Question - CV Forum

Types of Cyber Crime: Hacking, Phishing, Malware 2026
Priyanshu Bhatt Jan 12, 2026 1.2K Reads

As technology continues to evolve and advance over the years, there is an increasing surge of cybercrimes. The more the industry develops over time, the more cyber crimes will grow in frequency and advancement. Every business needs to manage the same with proficiency, and by this, the need for professionals in the same field is rising at a higher demand.
Professionals in the dynamic realm of cybersecurity have thorough practical and theoretical knowledge of cybersecurity principles and practices, and their expertise leads to organizational security enhancements. Cybersecurity is a broad term that needs to be addressed in an in-depth way, as the principles and practices associated with it are more complex than they sound.
Understanding The Real Meaning Of Cyber Crime
Cybercrime is a digital criminal activity that has peaked over the years due to the digital shift of all forms of industries after COVID-19. The upsurge of digital crimes such as online fraud, money theft, information leaks, etc, is the core of this, and these issues need to be addressed proficiently.
In this information-driven world, where data is leading everything, properly and securely storing it becomes essential for every business in every industry. However, after those safety measures, cybercrimes are still happening around the globe, and data theft is still going on.
In simple words, cybercrime is the unethical use of technology to gain dishonest profits. From white hat to grey to black, it revolves around data, as the key to every beneficial tactic is data. So, organizations should strategize proper actions and implementation to develop effective strategies to overcome these types of major issues.
So, to understand the complete realm of cyber crimes precisely, both practical and theoretical knowledge is essential, as proficiency in the same leads to the betterment of the crucial data stored. However, to get a brief overview of the structure and how everything works, you can have a look at the fundamental information below.

Major Types Of Cyber Crimes
In the digital era, where cyber crimes are increasing and advancing day by day, they are divided into 3 separate categories. Understanding these major classifications should be the core of every individual associated with cybersecurity. So, the 3 types of cyber crimes are as follows:
1) Hacking
Hacking is the unethical process of getting unauthorized access to digital gadgets and software such as smartphones and computers. This process is done by cyber criminals for various reasons, such as collecting information, getting financial gain, and political reasons
All these cyber criminal activities are known as hacking. In simpler words, hacking is the act of attempting unauthorized access to devices for a variety of reasons, and it is not always considered a malicious activity, but it is commonly considered an illegal activity.
Methods Of Hacking Employed By Hackers
In the current world, where technological advancements are very frequent, there is a rise in hacking methods that are employed by hackers all over the globe. Some of the major strategies and tools used by them are as follows:
-
Denial of Service (DOS): Denial of Service or simple DOS is one of the most common malicious or cyber activities that is used to disrupt the network or service by excessive traffic of data. It is among the most common cyber attacks in which several machines target one machine by targeting it with system traffic. The majority of these attacks are ignored by the public, as the individuals or organizations seem to note this issue as normal, as no such harm is done in the overview. However, the impact this attack plays, and the loss they bear, is of quite high value as a large amount of data and traffic impacts the function of the attacked device.
- Botnets: The term botnets is much more complex than it sounds, but it is as easy to understand as anything else. In simpler terms, the botnet is a group of computers that is being affected by bad software. To easily understand this, it is a group of robots managed by one single person who is known as the “bot-herder. In this, each computer, i.e., the robot in the booth, is known as a bot. As the bot-header can handle any set of bots, they can perform illegal activity like some sort of criminal action on a large scale.
-
Browser hijacks: Browser hijacking is a hacking activity that targets web browsers to change their web activity with unauthorized access. It is an illegal activity that is carried out to redirect the website the user is looking for to a website that needs illegal traffic. This activity is one of the harmful activities as it could destroy the backend functioning of a sub-web browser. In addition to this, most people also call it a browser redirect virus as it redirects one browser to another without authorized access.
-
Ransomware Rootkits: A ransomware rootkit is a kind of malware that lets hackers remotely access devices and install ransomware. In simpler terms, ransomware is something that has to be paid to attackers to make the website that has been attacked free. This kind of malicious activity is on the rise due to the harm it causes to the individual or organization that has been attacked. They are most commonly used to steal banking details such as card details, passwords, OTPs, etc. Moreover, rootkits are quite difficult to track and catch as their system files and identities are hidden.
-
Viruses: Viruses, or simply computer viruses, harm internal software and can threaten the overall functioning of the computer system. This kind of harmful software is highly transferable, and it can even harm other devices connected or associated with the harmed device. The goal of viruses is to create major problems to eliminate the peak performance of devices, making them deteriorate over time. In order to easily understand the term computer viruses, in a general sense, it is like any other virus that could spread and affect the functioning majorly.
-
Trojans: A Trojan is a sneaky computer program that pretends to be a good activity, but in reality, it is completely different. In simple terms, they pretend to be a free service, software, video, music, etc, but turn out to be actually the opposite, which actually and eventually harms devices.
-
Worms: Worms are generally known as self-replicating viruses as they use the existing flaws to spread across the network. In basic terms, it is a form of virus that exploits the weakness to steal valuable information and data through networks. They solely replicate them without human intervention, and that makes it one of the most harmful viruses available on the internet. Moreover, they can consume large amounts of memory, which makes them even more threatening to servers, software, and devices.
2) Phishing
Phishing is the process whereby the attackers defraud the targets into divulging personal details, including usernames and passwords, credit card numbers, and addresses, among other details. Phishing usually goes hand in hand with e-mail, messages, or posts on social networks and bills itself as a message from banks, authorities, popular online services, etc. These freshly devised fake messages contain a chief intent of stimulating the targets into clicking on the provided links or inputting their details into the said fake websites.
Types of Phishing Attacks
Phishing attacks are particularly perilous and tend to tap into the most fundamental human instincts of trust and interaction. Well, generally, security measures can safeguard against numerous sorts of cyber threats, but phishing attacks are quite proficient in exploiting people’s willingness to receive seemingly trustworthy-looking messages. Phishing may be of several types, but all have different features in them, as highlighted below.
- Deceptive Phishing: Phishing is the most prevalent type of cyber threat, and of the many subcategories, the most prevalent is deceptive phishing. Here, the attacker pretends to be representing a particular organization or even an individual with a view to obtaining some sensitive information from the victims. The attacker may use an innocent-appearing entity, such as a bank, and send an email requesting the receiver to update their account information in a link provided, which is a phony link. It just intends to deceive the victim, get their credentials, and then the attacker could use them in any way they desire.
-
Spear Phishing: Spear phishing is nonetheless even more personal, and the attacker takes a personal or organizational approach in sending the e-mail. In contrast to ordinary phishing emails, spear phishing messages usually have relevant information about the target that gives them authenticity. Cybercriminals get the target’s message to appear legitimate by using information obtained from social media accounts, corporate websites, and similar places. Remember that the outcome or purpose of most scams is to make the odds of the unlucky victim falling for it go up.
- Whaling: Whaling is a specific type of Spear phishing attack that targets senior or important personnel within an organization, including executives, managers, and decision-makers. The attacker masks himself/herself as one of the recipient’s co-workers or business associates, and he/she uses quite appropriate and convincing language to deceive the recipient into revealing secret details or sending his/her cash. Whaling attacks pose a high risk to a business because the perpetrators focus on the key management employees or team members who have access to the company’s valuable data and its funds.
-
Pharming: Pharming is more complicated than phishing because the attacker modifies the Domain Name System records to route the victim’s connections to a fake website that is indistinguishable from the real one. This is done through the manipulation of issues such as the DNS settings of the victim or the invasion of the victim’s computer with a malware program that alters how URLs are resolved. The purpose is to obtain the login credentials or any other information from the users who were expecting to visit the genuine site.
3) Malware
Malware is another term for ‘malicious software’ designed to compromise, harm, or invade private computer systems, networks, or devices. Malware is different from hacking in that, instead of attempting to gain unauthorized access to a computer system, malware seeks to take advantage of current access to perform malicious actions that include stealing, deleting, or controlling the computer system resources.
The term ‘malware’ refers to all sorts of evil programs that can harm a computer, including viruses, worms, ransomware, etc. Every type of malware has its characteristics and objectives, which is why people and corporations need to know the existing types of malware and how they work.
Types of Malware
Malware can be described as any intrusive software, and it is diverse and characterized by its type and goal. Below are some of the most prevalent types of malware:
- Viruses: A virus is a type of malware that invades a legitimate file or program and proliferates to others in the system or to another device on execution of the infected file. They can alter or delete data, reduce its accessibility, or make systems tortoise slow or completely unresponsive. There is always a risk of receiving it with an email attachment, downloading the virus from an infected download, or even visiting infected websites. Viruses are essentially programs whose operations are primarily detrimental and are usually made to corrupt or delete files in a particular target system.
-
Worms: While viruses need a host file to be coded to propagate, worms are programs that perpetuate themselves over networks independently. Worms take advantage of weaknesses within a system to reproduce and affect other hosts, and often simply use up resources in a network. Worms are meant to replicate this, winning the race of infecting the available systems and networks by flooding them with traffic.
-
Ransomware: Ransomware is a specific type of malware that tends to deny access to a person’s files or even the functionality of some of their devices. The attacker then threatens to sell the decryption or to destroy data irretrievably and instead asks for a ransom in cryptocurrency. Ransomware is a form of malware that affects anyone and can be used to blackmail individuals, companies, and even the government, causing huge losses, theft of data, and organizational disruption. An example of ransomware that recently attracted much attention is WannaCry and NotPetya.
-
Spyware: Spyware is a form of virus whose main function is to gather information from a user’s computer without the victim’s knowledge. It is usually employed in identity theft, credit card fraud, scams, and corporate spying. Spyware can monitor a user’s computer usage, capture login information, take a snapshot, and log keystrokes. Spyware programs can be downloaded from vulnerable sites or received as files with viruses in an e-mail attachment.
-
Adware: Adware is a type of malware that alerts a victim by displaying unbearable advertisements on his or her device. Despite its relative benignity, adware, in essence, may decrease the system’s performance, initiate the redirection of the browser, and install other dangerous software. Some types of adware monitor a user’s activities to display ads, thus invading users’ privacy. It is a more annoying type, but it does add to system threats and can cause lots of issues with overall system performance.
- Trojan Horses (Trojans): A Trojan is a kind of virus that hides its real function and purpose behind an innocuous program or file. With Trojans, the implications attach once installed and can spy, scan, corrupt data, obtain unauthorized access, and open other backdoors for Trojan activities. Trojans are different from viruses or worms in that the latter reproduce themselves; Trojans need the user’s action to run them: that is why social engineering is a key element of Trojan strategy.
- Rootkits: A rootkit is malware that places itself deep within an operating system and is designed to remain unnoticed and continue to have administrative-level access to the infected computer system. Having been installed, a rootkit enables the hacker to take full control of a device without the knowledge of the user. Rootkits are extremely hard to install and remove; they camouflage themselves by changing system files and executable processes, which is why they represent a huge threat.
- Keyloggers: A keylogger is a form of virus that captures all the keys that are pressed on a particular device. Defining, usually, keyloggers focus on one’s inputs, thus retrieving passwords, credit card numbers, and personal messages. The most damaging activity of cybercriminals is when they employ keyloggers to obtain login details with the intent of using identity theft by accessing one’s accounts.
- Backdoors: Backdoor malware provides the hacker with unauthorized access to a system, and regular authentication/Security measures will not be relevant. Backdoors allow attackers to gain access to the system to steal the data, introduce other malicious programs, and take control of the given system remotely. Backdoors are implanted by other forms of malware, including Trojans, and they give the handler persistent and invisible access to affected computers.
Some Examples Of Cyber Criminals
In the dynamic realm of cybersecurity, there are quite a lot of cybercrimes and criminals. Some of the major cybercriminals listed are as follows:
-
Cyberstalkers:Cy:berstalkers are people who use digital devices, applications, and software to threaten and harm others. They use major platforms such as email, applications, and other platforms to navigate the unethical process.
-
Cyber terrorists: Cyber terrorists are digital criminals who cause disruption and violence to threaten others. They use cyber-attacks to influence others for political and social reasons.
-
Black hat hackers: Black hat hackers are cybercriminals who use computer networks and systems with unauthorized access to cause harm and steal data. Black Hat hackers are also known as crackers in the cybercrime world.
-
Scammers: Scammers are people who use fraud strategies to gain personal and financial information. Their core fraud is to earn money for personal agendas.
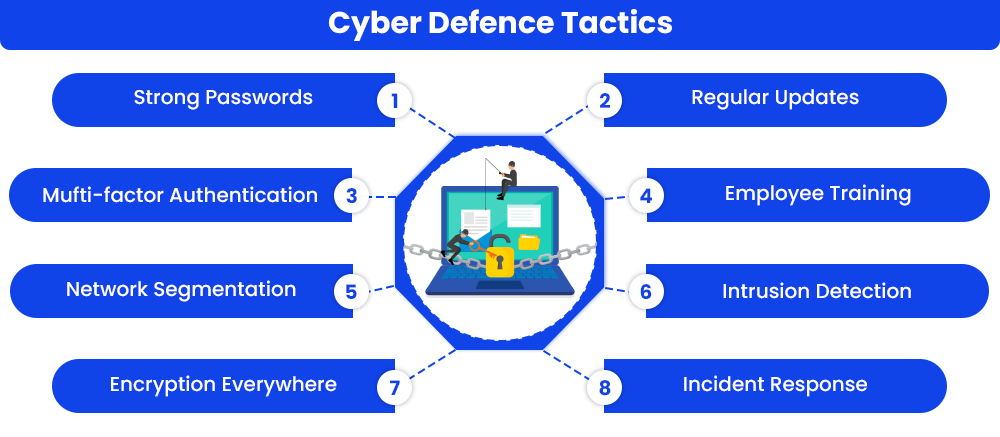
10 Effective Ways To Prevent Cyber Attacks
There are many ways to prevent cyberattacks, and some of the major ways every individual should consider in their day-to-day functioning are as follows:
-
Phishing Awareness Training: Proper training sessions should be given to employees and individuals about why phishing is harmful, which is one of the essential aspects for organizations. Through these beneficial training campaigns, individuals will get to know about the empowering and detecting techniques and strategies to analyze and beat phishing attacks.
- Encrypt Data: Data encryption should be the priority of every organization, whether private, government, or general. All data that is available should be encrypted and served on safe servers. This will lead to the elimination of access for attackers as strong encryption denies the readability of data and information that is being targeted.
-
Compromised Credentials Detection: Compromised Credentials Detection is a beneficial process that identifies the time at which users log in to information and when the act of data leak has occurred. If malicious activities are addressed at the time they happen, it will create a tiny impact because it is eliminated then and there. In technical words, this created a baseline for normal activities in the system and administers accounts that have been used.
-
Use Multi-Factor Authentication: Using multi-factor verification (MFA) in systems is considered one of the best practices to prevent cyberattacks. By this, the attackers have to know the additional and unique piece of the combination to enter the system full of crucial data and information. Biometrics, specific device requirements, etc, are some of the major examples of multi-factor verification.
- Ransomware Prevention: By creating a three-point plan, organizations and individuals can manage to prevent ransomware attacks. The process includes reducing potential impact, minimizing the surface that has been attacked, and lastly, pinpointing the gaps in the existing plans. In simple terms, ransomware prevention is the beneficial process of preventing the risk of ransomware by strategic planning and techniques.
-
Use Endpoint Protection: The main target of cybercriminals is end users, as the code to access is easy to get. So, in order to prevent that, every end user should employ endpoint security to protect access to systems. The endpoint protection should be integrated with effective tools and software like SIEM to monitor and address threats before they create a major impact.
- XSS Attack Prevention: XSS, or cross-site scripting, is a web attack that injects some sort of harmful code into devices through websites or applications. In simpler words, attackers send malicious code or links to users so that if the user clicks on them, all the data stored will be directly sent to the attacker's domain system. In order to prevent this, a filtering policy would help a great deal, as it catches malicious scripts in a wider range.
-
Threat Intelligence Program: A threat intelligence program is a system strategy that analyzes, shortlists, collects, and makes the most out of the data available to prevent and detect cyber threats. In technical terms, it creates a hub to feed the security functions to manage and prevent threats. Continuously feeding data into these systems will lead to the prevention of cyber threats without human effort.
-
Implement Network Deception Technologies: Network deception technology is a strategy associated with cybersecurity to prevent attacks on organizations' assets and data in general. With this beneficial strategy, organizations can detect threats beforehand, which will eventually reduce damage and protect the assets of the organization. It works on a basic principle, i.e., deploy decoys as these realistic codes placed in the service help prevent cyber attacks.
-
Mobile Device Management Solution: In the current world, almost every organization is working digitally, and devices like mobiles, laptops, and computers are running daily with a lot of information stored in them. So, to make a secure connection and to save the data from theft or loss, every device should be managed and enrolled by MBM or Mobile Device Management. This beneficial software or tool will help your devices wipe unauthorized access if your device is lost or stolen.
Why Are Cyber Crimes Increasing?
As you must be aware of the technological advancements over the years globally, the world has achieved so much in almost all domains of technology. With such a rise, the upsurge of cyber crimes is also increasing due to the short-term heavy profit it gives to the attackers. The crimes performed by attackers are no less than extreme general crimes, as the punishment for the same is prison, heavy fines, or both.
Some of the major reasons why it has increased over the years and continues to do so are as follows:
- Vulnerable Devices
- Personal Motivation
- Financial Motivation
- Political Reasons
And many more! The eventual goal of every attacker is to gain unethical profit out of these major reasons.
Conclusion
Summing up, the major types of cyber crimes, such as hacking, phishing, and malware, exist and pose a problem that targets everyone and every company. These types, in their various forms and ways of delivery, can be a real threat, starting with stealing information and ending with system failure. By realizing the various forms of cyber crimes and putting into practice secure network protection, people and companies can prevent themselves from the threats stemming from virus invasions.
FAQs (Frequently Asked Questions)
The three common and major types of cyber attacks are: Hacking, Phishing, and Malware.
A malware attack is a cybercrime where malicious software performs unauthorized access in the systems, devices, and software of victims. This type of attack is categorized into several types, such as ransomware, spyware, etc.
Some of the types of malware attacks are as follows:
- Worms
- Ransomware
- Spyware
- Adware
- Trojan
- Rootkits
- Keyloggers
- Backdoors
The full form of Virus is Vital Information Resources Under Siege.
One major example of phishing is when a person receives an email from their bank account-associated application, stating that their account has been deactivated, and unless and until they enter their card details, they won’t be able to continue with their account. The link in that email is the major issue from where all the information gets stolen.
The top 5 cyber threats that organizations should focus on are as follows:
- Social Engineering
- Third-Party Exposure
- Cloud Vulnerabilities
- Ransomware
- IoT
No, Malware is not a virus. It is a type of software that is designed to cause harm to computer systems, devices, and software. It spreads from one computer to another threatening the overall functioning of each.
Phishing is not malware as malware is software and phishing is a method to grab information unethically. But phishing involves methods of malware as it makes the overall process of acquiring data easy for attackers.

3 Years of Experience | Content Specialist I Copywriter
Writing what Google loves, and students need.
Every query is essential.
Our team of experts, or experienced individuals, will answer it within 24 hours.
Recommended for you
Tired of dealing with call centers!
Get a professional advisor for Career!
LIFETIME FREE
Rs.1499(Exclusive offer for today)

Pooja
MBA 7 yrs exp

Sarthak
M.Com 4 yrs exp

Kapil Gupta
MCA 5 yrs exp
or



Career Finder
(Career Suitability Test)
Explore and Find out your Most Suitable Career Path. Get Started with our Career Finder Tool Now!
ROI Calculator
Find out the expected salary, costs, and ROI of your chosen online university with our free calculator.
