Cyber Security as the name suggests is all about securing the cyber components like computer devices, networks, and servers, as well as the data within them from illegal invasion in the form of hacking by cybercriminals.
With the onset of the era of Digitalisation, a lot of opportunities have been opened for all and especially businesses and enterprises. From internet banking to online shopping to online education, everything is just a click away. However, as it has been rightly said that every good thing comes at a price. The more you connect to digital assets, the higher is the risk of security vulnerabilities of your confidential and sensitive data.
Now, the question arises- how are big companies with a lot of confidential information securing their data and combating cyber threats? The answer is Cyber Security. So what is Cyber security?
What is Cyber Security?
To explain in simple terms, Cyber Security is an umbrella term that includes technologies, processes, and practices specifically designed to protect various digital components, computer systems, networks, programs, and data from attack or damage. This attack or damage can be through unauthorized digital access or misuse of authorized digital assets.
Cyber Security aims at reducing the risk of cyberattacks to protect organizations and individuals from the intentional as well as unintentional exploitation of security weaknesses, systems, networks, and technologies.
Let us understand in even simpler terms with the help of an example.
Meet Riya. Riya often shops from an online shopping website called Shopkart. She has her personal information like email id, phone number, address, and credit card details saved on the website server to enable a faster and hassle-free shopping experience.
One day Riya received an email from Shopkart stating that she is eligible for a special discount voucher. In order to receive the coupon code, she was asked to fill in her Shopkart account credentials. This did not seem fishy at the time as it seemed like an account verification step. However, she was knocked off her feet when a substantial amount of money was wiped out from her account.
How do you think this happened?
Well yes, the email from Shopkart that Riya received, was a fake and her Shopkart account witnessed unauthorized access from a third party.
This is the kind of attack which is known as a cyber attack and the person who carries it is known as a Hacker. Could Riya have prevented this attack? Indeed, she could have, with the help of Cyber Security!
However, the type of cyber attack discussed in the example below is not the only kind. There are various types of cyber threats that individuals and organizations are exposed to. Let’s understand them in detail. Read: Industry Experts Cyber Security Interview Questions!
Types of Cyber Threats
Before moving on to the types of cyber threats, let us first understand what a cyber threat actually is. It is any malicious practice that aims to unlawfully access and steal confidential data, attack digital operations, or damage the digital assets of an individual or organization.
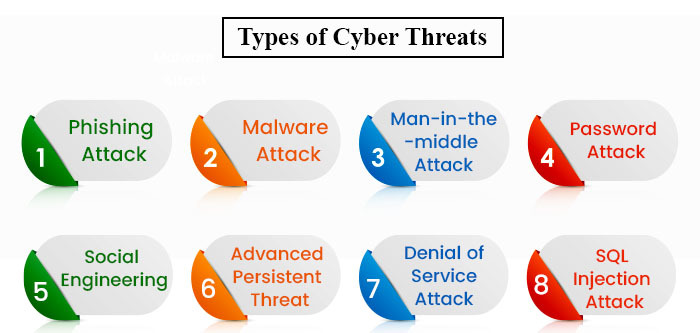
Let us first look at the cyber-attacks that individuals like Riya are exposed to.
1. Malware Attack
Malware stands for malicious software. It is the most common threat of the lot. It is generated through a link or an attachment which is usually sent through an email or a legitimate-looking download attachment. Once you click on the link or download the attachment, the malware corrupts the system of the user and gains unauthorized access.
Malware attacks are also of the following different types.
- Virus
Just like the medical virus you know, a digital virus gets attached to a clean file on your computer and spreads itself throughout the system infecting other files as well with some malicious code.
- Ransomware
Just like the name suggests, it is malware that infects a user’s files to lock them down and threaten the user of erasing the files in exchange for ransom.
- Spyware
Again as the name “Spy” suggests, this malware secretly records what the users do on their computer to extract important sensitive information like credit card details to maliciously use this information.
- Trojans
This is quite a dangerous type of malware as it is disguised as legitimate software and users are tricked into uploading it on their systems. Once uploaded, Trojans corrupt the entire system or collect confidential data.
- Adware
Adware stands for Advertising software. These are usually advertisements and pop-ups that show up on your computer system. Some of these can be malware that can hide on your device to monitor your online behavior and target you with specific ads. But then you must be wondering how are these a threat. It is because they have the capacity to slow down your device, hijack your browser, and even install other malware such as viruses and spyware.
- Botnets
You must have heard of bots used to comment on social media platforms. Yes, these are malware. A botnet is a network of many malware-affected computers. Cybercriminals use Botnets to perform digital tasks (specifically on the internet) without the permission of the user.
2. Phishing Attack
Just like how it sounds, in a phishing attack, a hacker throws bait at you to grab it and when you do, they steal your sensitive confidential information like passwords, login credentials, credit card numbers, and other bank details.
These are usually carried out with the help of fraudulent emails which appear to be coming from a legitimate source. This is to install one or more of the malware discussed above to steal data.
3. Man-in-the-middle Attack
This type of attack happens during two-party transactions. Here, the hacker gains access to the information path between the user’s device and the second party’s website server. With this, the hacker’s computer takes over the user’s IP address and with this, it is game over for the user. The hacker can now install malware, after which the communication line between the user and the website is secretly intercepted and the data can be easily stolen and used maliciously. This usually happens because of unsecured Wi-Fi networks.
4. Password Attack
This is one of the easiest ways to hack a system. Hackers crack the user’s password using either common passwords or trying all possible alphanumeric combinations with the help of coding. Hence, it is always recommended to set unique and strong passwords using not just alphabets and numbers but other special characters as well.
5. Social Engineering
Social Engineering is a cyber threat that first involves human interaction. Here, people obtain personal information like phone numbers from social media and then trick and manipulate people into revealing confidential information. These people even solicit monetary payments.
Social Engineering is often combined with other cyber threats listed above. These people manipulate users into clicking on malware links or make you trust sources that are actually adwares, spywares, or other malicious cyber threats.
Cyber attacks are not just confined to individuals but also to public and private organisations. The cyber attacks carried out in such organisations are even more deadly and result in colossal losses. Ransomware is one such cyber attack aimed at wealthy organisations in order to extort money.
Let’s look at a few of the cyber threats that companies are subjected to.
1. Advanced Persistent Threat (APT)
Various public sector organizations and large corporations face the Advanced Persistent Threat (APT). In this type of attack, hackers gain access to the organization’s network. They access it for a prolonged period of time in order to continuously gain confidential information.
2. Denial of Service Attack
In this type of attack, the networks of the organization are flooded with traffic with an aim to leave legitimate service requests unattended. A variant of this is the Distributed Denial of Service (DDoS) attack where multiple systems are used to launch the attack. This DDoS originates from a computer network. After carrying out the DoS, some hackers use this time until when the network is disabled to launch other attacks and malware. DDoS is also a type of Botnet which is capable of infecting millions of systems with malware.
3. SQL Injection Attack
When a cybercriminal manipulates a standard SQL query in a database-driven website, it is known as an SQL Injection attack. The hacker inserts some malicious code into the server which in turn releases the information of the database to the hacker. This attack is done so that hackers can view, edit, and even delete tables from databases.
Types of CyberSecurity
Hackers today are quite advanced and up-to-date with the latest technologies. Therefore, it is very crucial for organizations (both private and public) to have a strong cybersecurity strategy. This means there should be multiple layers of protection to ensure security against cyber threats.
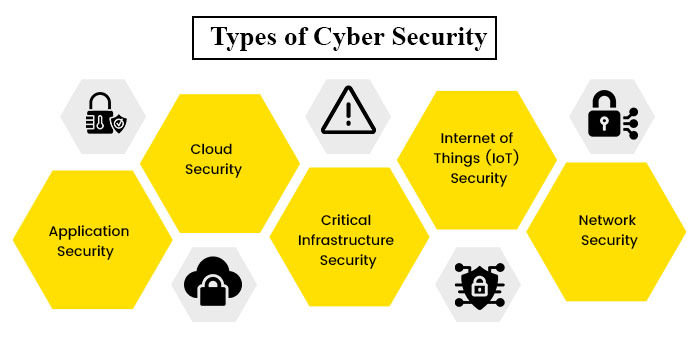
Following are the common types of Cyber Security domains that every organization must possess.
1. Application Security
This security process helps to protect the applications that are operating on the device and in the cloud. This security is built within the application at the design stage only considering how the data is going to be handled or the user authentication, etc. The application security hence addresses the vulnerabilities that are a result of insecure processes that happen during the designing, coding, or publishing of an application or software or website.
2. Cloud Security
Cloud is like virtual storage of data, networks, applications, and servers that can be accessed via the Internet. Cloud security is the domain of cyber security that deals with securing data and applications within the Cloud. It also protects the cloud data when it is in use and in motion, i.e., when the data travels to and from or within the cloud in order to ensure customer privacy as well as regulatory compliance standards.
3. Critical Infrastructure Security
As the name suggests, Critical Infrastructure Security protects any digital assets related to national security, economics, and public safety. These digital assets include computer systems, networks, and servers of various government and public sector organizations. It is a very crucial cyber security as it deals with securing data of national importance.
4. Internet of Things (IoT) Security
If you have heard of automatic cars or electric appliances at home like lights and refrigerators that can be operated remotely through voice commands or other such methods, then these are all examples of IoTs. IoT is the network of physical objects that can collect and exchange data in real-time with the help of embedded softwares, sensors, and other technologies.
Other IoT devices are fire alarms, thermostats, lights, doors, and other such appliances. A breach in the security of these IoTs within an organization can cause huge infrastructure losses and can even compromise the security of the building. Hence, IoT security is used to secure networks and all the smart devices connected to the IoT.
5. Network Security
Network Security ensures the protection of computer networks from cyber intruders. This security detects and resolves vulnerabilities that affect an operating system as well as network architecture. Cyber attacks can affect any part of the network architecture be it servers, hosts, firewalls, network protocols, and both wired and wireless (Wi-Fi) access points.
Who Needs Cyber Security?
If you think that it is only the big private and public corporations that need cyber security then you are mistaken, my friend. Anybody who uses the internet irrespective of their devices needs cyber security. It is true that rich companies are more exposed to the dangers, however, most cyber attacks are automated which means that they target vulnerable networks or systems rather than specific organizations. This makes common people more vulnerable because they do not spend tons of money on cyber security as rich corporations do.
Challenges of Cyber Security
New technologies help us evolve and grow in various ways, however, they also pose new challenges to cyber security. This is because, with evolution, software constantly changes with every new update. These new modifications often introduce new issues which make the system or network vulnerable and exposed to cybercriminals. Evolving IT infrastructures involve a whole new set of designs and implementations. This results in new forms of vulnerabilities of which the organization is usually unaware of.
Why Is Cyber Security Important?
As you know that our world is moving towards complete digitalization. Any sector you know of is becoming digital be it government organizations, hospitals, educational institutions, military, finance, energy industry etc. The crucial information within these organizations such as economic information of the country or national/border security information etc, is becoming digital as well.
This information is stored on the omnipresent internet and has to be accessed through digital communication networks. Such sensitive information holds great value to criminals such as terrorist organizations or hackers from other countries. The motives of such attacks are many. From monetary gains to damaging a company’s reputation, to tampering with crucial data such as the one that involves national security.
Consequences of Cyber Attack
There have been hacking incidents with big organizations such as Yahoo, Equifax, US Securities and Exchange Commission (SEC) and the Mumbai Power Hacking incident has resulted in massive losses and the compromising of data of hundreds of millions of users. Even more dire consequences of cyber attacks can be when there are cyber attacks on organizations such as the military. In such cases, national security is at stake. Similarly, cyber attacks on the finance sector of a country can lead to colossal losses of national monetary assets. An example of one of the biggest cyberattacks in recent history is the Wannacry Ransomware Attack of 2017 which affected over 2 lac computers across 150 countries.
A Career In Cyber Security
Amidst a plethora of cyberattacks, it is indeed a challenge for organizations with several networks and servers to ensure complete security. This is quite a difficult task and so cyber security professionals are hired in order to work on identifying cyber threats so as to secure the company’s network.
There are multiple job roles in the field of Cyber Security. And these jobs are quite lucrative as the largest and richest companies in the world are in need of cybersecurity experts. If you’re wondering why then let us understand with this example.
For instance, you find a product on Flipkart and plan to buy it. While checking out, you are given options to pay through your Debit or Credit card or through UPI. And if you shop often, then most of this information is usually saved on the website.
With millions of users sharing such sensitive information over the platform, ever wondered how Flipkart and other biggies like Amazon, Myntra, etc try to secure this information? How do Google and Facebook manage to protect the confidential personal data of their millions of users?
From robust and renewed privacy policies to security-focused patents to the use of Artificial Intelligence (AI), each company is expanding its focus on data protection to encourage and build user trust. And with the increasing advancements in today’s tech-oriented digital world, Cyber Security threats will also advance and keep getting more complex as hackers easily learn to adapt to security strategies.
Hence, this is bound to increase the widespread requirement of cyber security by companies that will be willingly paying more than ever to recruit highly skilled cyber security professionals in order to secure their important confidential and of course quite vulnerable assets from cyber attacks.
Jobs In Cyber Security You Need to Know About
With the increase in the production of global digital data, it is anticipated that cyber-attacks will quadruple in the near future. Organizations are going to need cyber security professionals who can protect these organizations from these cyber threats.
If hacking fascinates you then the role of an Ethical Hacker is something to be explored. Ethical hacking professionals try to expand network vulnerabilities just like how a hacker would do but only to identify those vulnerabilities and resolve them for protection against an actual cyber attack.
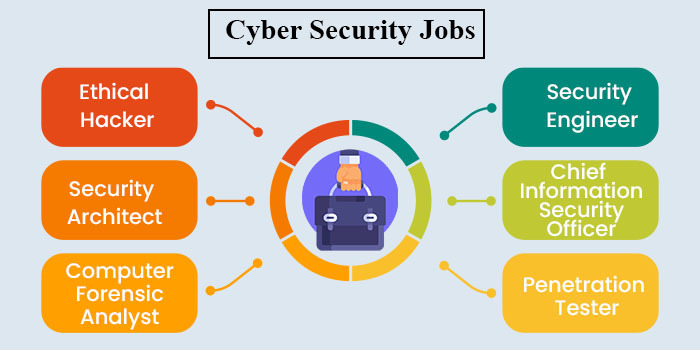
However, if you are looking to design robust security structures then the role of a Security Architect is more apt. Another popular job is that of a Chief Information Security Officer (CISO). This job role plays a crucial part in enterprise security. The CISO is entrusted with the overall safety of the information in an organization. Read: Cyber Security Salary for Beginners and Experienced!
A career in the field of cyber security is lucrative and a very smart decision for professionals now. The following table lists some of the common job profiles in the field of cyber security along with their salary.
| Cyber Security Job Profile | Cyber Security Average Base Salary per year (in INR) |
| Chief Information Security Officer (CISO) | 22,13,695 |
| Ethical Hacker | 5,81,159 |
| Cybersecurity Engineer | 7,43,743 |
| Security Architect | 21,44,029 |
| Penetration Tester | 6,17,313 |
| Computer Forensics Analyst | 7,00,000 |
Top Skills to get into Cyber Security
If you’re new to the field or looking for a career transition, there’s just so much information out there that it is just so hard to get started. Having theoretical knowledge with the help of different courses is indeed very valuable but what is important are your skills and experience.
This is because this is the kind of field where what you CAN DO makes you more successful than what you KNOW. Solving technical problems is THE way to earn the trust and confidence of the people you work with.
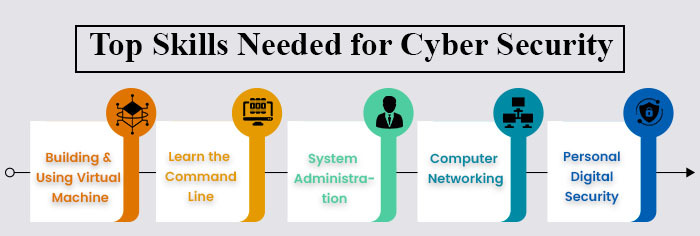
Following are some of the skills you need to know to get into Cyber Security.
1. Building and Using Virtual Machine
Virtual Machines or VMs are operating systems that run on top of your existing or ‘host’ Operating System (OS). VMs are commonly referred to as ‘guests’ and are managed by software called a “Hypervisor”. It helps you manage and allocate resources like CPU, Memory, and Disk Space on your guest.
VMs let you become platform-agnostic. This means you are no longer limited to just one OS and its tool. As a pro, you should be well versed in ALL types of Operating Systems and comfortable working with any platform. This maximizes the scope of your skills and makes you efficient in any situation.
What you can do using VMs
- You have the flexibility to train and research in an isolated environment without affecting your main driver.
- Quickly take snapshots of a guest OS and also restore it back to the earlier state.
- You can easily open a suspect file you received.
- Practice configuring a server.
- Slinging exploits at a target.
Some of the popular hypervisors are Hyper-V by Microsoft, Virtualbox by Oracle, VMWare, and KVM.
2. Learn the Command Line
The Command-Line also known as a “Shell” is the simplest and arguably the most efficient way to interact with an Operating System. Many of the most useful tools don’t have a graphical interface to point and click. Mastering the Command Line expands your arsenal and lets you get more done with less.
Advantages of Command Line
- You can use scripting and automation to tackle repetitive tasks that would otherwise waste a lot of your time.
- Automating your workflow by learning the Command-Line makes you a tremendously valuable asset to your team.
- You can start with BASH or the “Bourne-again Shell” as it comes default with every Linux distribution.
Note- If you work in an environment where Windows is the primary OS, then you must definitely learn Powershell as well.
3. System Administration
Anybody who uses a computer or a smartphone, from your parents to an IT wizard, is really a sysadmin but just at different levels. System Administration includes configuring and maintaining of computers, whether personal devices or high-power servers.
System administration is all about knowing your computer or your device platform and its various tools inside out to be able to help others who don’t. If you know each and every detail of your platform, other things will come to you easily as well.
4. Computer Networking
Computer Networking is the heart and soul of it all. It is about understanding how different devices interact with each other and how the data goes from one point to another.
A strong foundation in networking will make you a rockstar troubleshooter at whatever you do, be it red teaming, defending, or running day-to-day IT ops.
5. Personal Digital Security
The cybercrime industry is booming as a result of growing digitalization. As technology becomes more intertwined with our lives, from internet-connected cars to refrigerators, the vulnerabilities and attack vectors are gonna increase more and more. So, if you wanna go deep into cyber security, there’s no better place than with yourself. From passwords and encryptions, to secure comms, stay up-to-date with the latest security news and best practices.
Do I Need to Learn Coding before Cyber Security?
Cyber Security is a massive field, it’s huge, and it’s ginormous. There is however one common thread that will absolutely help you if you’re a new individual and if you want to break into the scene. If you’re starting in cyber security, you’re just starting out, what should you do? Well, the absolute first thing that you should do is try and pick up a programming language.
Now there are a lot of questions like “Hey, do I need to learn how to code to be an ethical hacker or a penetration tester or just to be in cyber security? There may be different answers to this. Some might say no, you do not have to while some say yes you absolutely should. Both are kind of right answers. However, the experts in the field would advocate that you’re going to be so much stronger if you do learn the language.
So now you must be wondering which language to start with? The knee-jerk reaction of the maximum of the industry experts to this question would be Python. Python is a fantastic and wonderful language to really get the ball rolling. It is easy to read and write, you can rapidly just crank out code to prototype and develop things and so much more. It has wonderful documentation so you can read and find a lay of the land. It has so many different integrations to do so much stuff with the already existing software. Read: What Is Data Science?
Whether you’re interested in Artificial Intelligence (AI) or Machine Learning (ML) or maybe if you’re interested in the whole blockchain craze, then Python will teach you the programming concepts, the fundamentals of variable, function, loop, conditionals, etc which are some of the basics that you absolutely need to know.
Secondly, Python is a scripting language which means it is interpreted. This means there’s another program that is kind of waiting in the background reading your code as if it were a script to act out on stage and then performing those actions and doing those things which makes it extremely easy to learn for the new users. Read: Data Science Course Online In India!
If you’re looking for a compiled language, something with which you can have a lot more control over what’s happening, then most people might suggest C or C++. However, there is a new hotness in the market now in 2026 called Golang. Short for Go Programming Language, Golang is crazy fast. It has so much concurrency and the ability to do multiple things at once. It gives you the same expressiveness that Python does as well as the same power and core functionality that C or C++ do. It can cross-compile and can very easily run on Windows or Linux or Mac.
Cyber Security Short-Term & Degree Courses
As already discussed before, Cyber Security has a great future ahead and so many universities have started offering related courses. There are many online universities as well which are offering short-term as well as long-term courses on Cyber Security. It is a smart move to pursue these courses if you are looking for a future in cybersecurity as it introduces you to the subject, teach you various fundamentals, and are extremely cost-effective.
You can take a look at the following colleges and the courses that they offer.
| Cyber Security Colleges In India | Cyber Security Course Type | Cyber Security Course Name | Cyber Security Course Duration |
| Jain Online University | Certificate Course |
|
3 months |
| Postgraduate Course |
|
2 years | |
| Manav Rachna Centre for Distance and Online Education | Undergraduate Course |
|
3 years |
| Amity Online University | Undergraduate Course |
|
3 years |
| Postgraduate Course |
|
2 years |
Cyber Security Course Fee Structure & Eligibility Criteria
The total program fee structure for all the cyber security courses mentioned above is explained in the table below for each university.
| Colleges for Cyber Security | Courses for Cyber Security | Total Fees for Cyber Security Courses | Cuber Security Eligibility Criteria |
| Jain Online University | Certificate Course – Essentials of Cyber Security | For National Students – ₹12,000/-
For International Students – $250/- |
The candidate must have a bachelor’s degree in any stream from a recognized university. |
| Certificate Course – Python for Data Science | |||
| MCA in Cyber Security | For National Students – ₹2,00,000/-
For International Students – $4,200/- |
The candidate must have a bachelor’s degree of a minimum duration of 3 years in any stream from a university recognized by UGC with at least 50% or equivalent marks (45% for SC/ST candidates). | |
| MCA in Cloud Computing | |||
| Amity University Online | BCA in Cloud and Security | Semester-wise payment – ₹2,20,000/-
Year-wise payment – ₹2,00,000/- One-time payment – ₹1,95,000/- |
The candidate must have completed class 12th in any stream from a recognized university. |
| MCA in Machine Learning (ML) | Semester-wise payment – ₹2,20,000/-
Year-wise payment – ₹2,10,000/- One-time payment – ₹2,05,000/- |
The candidate must have a Bachelor’s degree in any stream and must have Mathematics at 10+2 level. For those candidates who did not have Mathematics at 10+2 can apply after but only after qualifying the Bridge Course. | |
| MCA in ML and AI | Semester-wise payment – ₹1,76,000/-
One-time payment – ₹1,64,000/- |
||
| Manav Rachna Centre for Distance and Online Education | BCA in Cyber Security | Semester-wise payment – ₹1,56,000/-
Year-wise payment – ₹1,46,250/- One-time payment – ₹1,36,500/- |
The candidate must have completed class 12th in any stream from a recognized university. |
Read: Top 10 Cyber Security Colleges In India!
Cyber Security Course Admission Process
The Admission Criteria for all of the above-mentioned Cyber Security courses are quite simple. You can complete the entire procedure online comfortably from your home. You just need to follow the simple steps listed below.
Step 1- First you have to visit the official website of the online university through which you want to pursue your Cyber Security course.
Step 2- Go to the “Programs” section and then select the course you wish to pursue.
Step 3- Click on “Apply Now”.
Step 4- Fill out the application form and submit your documents as well.
Step 5- The final step is to pay the application fee. You can pay it via Credit card/ Debit card/ Net Banking. After your documents have been verified, you will be informed about your admission. Once admission is confirmed, you can pay the program fee and start with your program.
Hopefully, by now you must have got a clear idea of what Cyber Security is and how majorly it affects our world. If you’re into Computer Science and are tech-savvy, then planning for a career in Cyber Security is a very wise decision because of the vast and wonderful scope that the field accompanies. If you wish to pursue an online course in cyber security then you can go to the College Vidya website and find the best online colleges offering various courses in this field.







